

A cyber campaign targets industry/organization using phishing and malware. Key IOCs include specific IPs and domains. To mitigate, organizations should patch vulnerabilities, enhance email security, and deploy endpoint protection..
A recent system audit identified vulnerabilities in system/software, including outdated patches and weak configurations. Recommendations include updating software, enhancing security configurations, and improving access controls to mitigate risks..
Malware was detected, The infection would be removed, and affected files would be quarantined. Recommendations include running a full system scan, updating security software, and changing passwords to prevent further compromise..
Replacing a maintains the amount of lines. When replacing a selection. help agencies to define their new business objectives and then create. maintains the amount of lines. When replacing a selection. help agencies to define their new business objectives and then create.

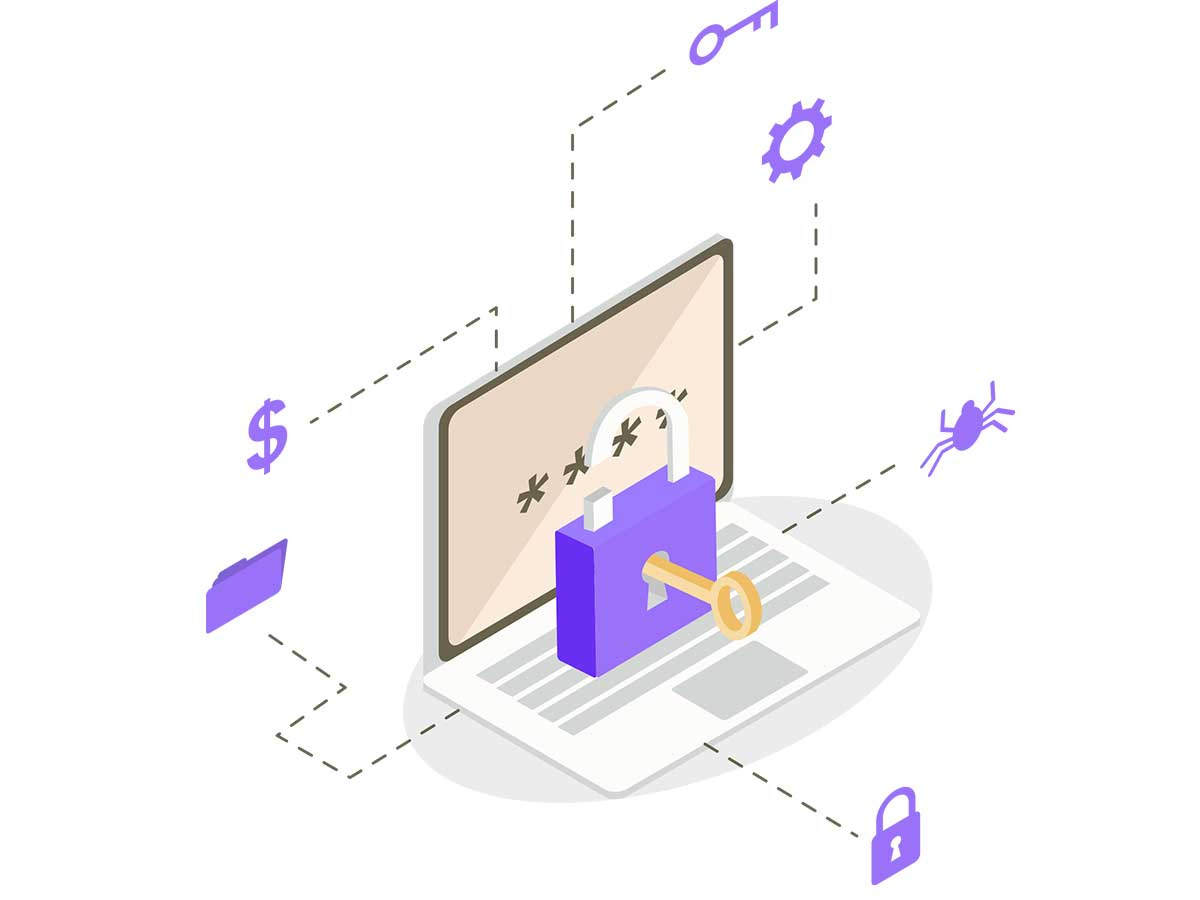
Cybersecurity solutions protect networks and data through threat detection and secure access, while data platforms manage and analyze data securely, ensuring privacy and compliance. Together, they safeguard assets and mitigate cyber risks.

And in general the content of dummy text is nonsensical. used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical. Dummy text is also used to demonstrate the appearance of different typefaces and layouts

Used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical. text is also used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical

Dummy text is also used. used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensica to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical.

And in general the content of dummy text is nonsensical. used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical. Dummy text is also used to demonstrate the appearance of different typefaces and layouts

And in general the content of dummy text is nonsensical. used to demonstrate the appearance of different typefaces and layouts, and in general the content of dummy text is nonsensical. Dummy text is also used to demonstrate the appearance of different typefaces and layouts
We have successfully delivered innovative cybersecurity and data solutions, enhancing our clients' security posture and operational efficiency. Our commitment to excellence has led to a track record of seamless integrations, reduced risks, and strengthened data protection across industries.
Interested in learning more about our services? Request a call back, and one of our experts will reach out to you at your convenience. We're here to answer your questions and discuss how we can help meet your needs. Simply provide your contact details, and we'll be in touch shortly!.
To successfully achieve our mission, we focus on clear goals, collaboration, continuous innovation, and adapting to challenges. By maintaining a customer-centric approach, leveraging cutting-edge technology, and fostering a strong team culture, we ensure consistent progress toward our objectives and long-term success.
When replacing a multi-lined selection of text, the generated dummy text maintains the amount of lines. When replacing a selection of text within a single line, the amount of words is roughly being maintained.
When replacing a multi-lined selection of text, the generated dummy text maintains the amount of lines. When replacing a selection of text within a single line, the amount of words is roughly being maintained.
When replacing a multi-lined selection of text, the generated dummy text maintains the amount of lines. When replacing a selection of text within a single line, the amount of words is roughly being maintained.

Stay updated with our latest developments, including new product launches, partnerships, and industry insights. We're constantly innovating to bring cutting-edge solutions and drive positive change in the cybersecurity and data sectors.